Lưu ý chung
Lưu ý 1: Cấu trúc lệnh netcat
nc <Machine IP> <port>
Lưu ý 2: Vì mỗi lần khởi động lại máy một địa chỉ IP mới sẽ được gán cho máy chủ CTF, nên IP của bạn không nhất thiết phải giống như trong bài nhé.
Lưu ý 3: Một điều khá dở của máy chủ CTF 100 Tryhackme đó là nó không lưu lại phần làm bài của bạn. Nghĩa là giả dụ như bạn đã làm được 10/19 câu của stage 1, bạn muốn để dành phần còn lại vào ngày hôm sau, thì qua ngày hôm sau, bạn phải làm lại những flags port knocking, là những flags mà khi bạn vượt qua, sẽ có những ports mới được mở ra cho bạn, ví dụ flag 7, thì bạn mới có thể làm tiếp được.
Lưu ý 4: Tryhackme chỉ cho thời hạn mặc định một máy hoạt động là 1 tiếng. Khi deploy máy, bạn có thêm click ‘Add 1 hour’ để có được 2 tiếng và bạn không thể click ‘Add 1 hour’ cho đến khi thời gian của bạn còn lại dưới 60 phút. Nếu bạn không gia hạn thời gian, máy sẽ tự động tắt khi hết thời gian dù cho bạn có đang làm việc với máy đi chăng nữa. Nên các bạn lưu ý nhớ theo dõi thời gian còn lại của máy nhé.
Lưu ý 5: ^C = ctrl + C
Link truy cập CTF 100:
tryhackme.com/jr/ctf100w1
Deploy the machine and telnet to the port 9999. Be sure to enter the port sequence which you obtained from stage 1.
After that, fire up your Nmap scanner with the following command.
$ nmap -Pn -v --min-parallelism 100 <Machine IP>
Looks like we have port 1111 opened on the machine. A further scan on the port leads us to an HTTP server.
Task 2-1: Flag 19 – Find and replace
A first scan reveals that port 9999 is open. Connect with nc 172.16.222.133 9999 and enter the sequence found at stage 1.
$ nc 172.16.222.133 9999
***************************
* Port knocking input *
***************************
Hi user, please enter the port sequence
The format is (can be more than 4): PORT PORT PORT PORT
> 31031 50010 7968 20010 6100
Something happen
Good luck!
$ nmap -Pn -v --min-parallelism 100 172.16.222.133
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-23 09:07 CEST
Initiating Parallel DNS resolution of 1 host. at 09:07
Completed Parallel DNS resolution of 1 host. at 09:07, 0.00s elapsed
Initiating Connect Scan at 09:07
Scanning 172.16.222.133 [1000 ports]
Discovered open port 9999/tcp on 172.16.222.133
Discovered open port 1111/tcp on 172.16.222.133
Completed Connect Scan at 09:07, 6.63s elapsed (1000 total ports)
Nmap scan report for 172.16.222.133
Host is up (0.0031s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE
1111/tcp open lmsocialserver
9999/tcp open abyss
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 6.66 seconds
Nothing happens when we connect with netcat on port 1111. A script/version Nmap scan reveals that this is a web service with Python:
PORT STATE SERVICE VERSION
1111/tcp open http SimpleHTTPServer 0.6 (Python 3.6.8)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: SimpleHTTP/0.6 Python/3.6.8
|_http-title: Site doesn't have a title (text/html).
Let’s try with a browser. We have a lot of alerts:
$ curl -s http://172.16.222.133:1111
alert!alert!alert!alert!alert!alert!alert!alert!alert!...[SNIP]...
Let’s get the file and remove the alerts to see if there is anything else:
$ curl -s http://172.16.222.133:1111 > alert.txt
$ sed "s/alert\!//g" alert.txt
flag 19:j4dnbdewgwgy5r7kjtnd
Answer: j4dnbdewgwgy5r7kjtnd
Task 2-2: Flag 20 – Robots
The flag is hidden inside the robots.txt. Basically robots.txt used to tell the search engine such as Google not to index a certain directory.
$ curl -s http://172.16.222.133:1111/robots.txt
Disallow:
/
/This_is_easy
/flag_20_2re645f4n2ex85g3b2fw
Answer: 2re645f4n2ex85g3b2fw
Task 2-3: Flag 21 – Bust the directory part 1
Every time you encounter an HTTP server (Not HTTPS), enumerate the server for any hidden directory. For starter, I recommend common.txt from dirb. Use the following command to start the enumeration.
$ gobuster dir -u http://:1111 -w /usr/share/dirb/wordlists/common.txt
$ curl -s http://172.16.222.133:1111/hidden/
<p>Not bad, you found the hidden directory</p>
<!--Always check the comment-->
<!--flag 21: 5tjdmdawe35dsacmunqa-->
Answer: 5tjdmdawe35dsacmunqa
Task 2-4: Flag 22 – Bust the directory part 2
Something enumerate the directory with common.txt alone is not enough. There are other wordlists available in the kali machine. Simply go to /usr/share in kali and you will found tons of wordlists. For this task, we are going to use big.txt from dirb.
$ gobuster dir -u http://:1111 -w /usr/share/dirb/wordlists/big.txt
It going to take a while. After that, we get another hidden directory.
$ curl -s http://172.16.222.133:1111/capture/
<p>Not bad, you found another flag</p>
<p>flag22: 35x7axg8xd7n4geyxp2t</p>
UHJvY2VlZCB3aXRoIHRoZSBuZXh0IGNoYWx<style></style>QMFZXG53POJSDUIDUNBSV6ZLOMQ======
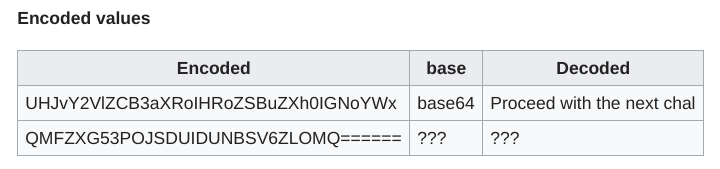
Answer: 35x7axg8xd7n4geyxp2t
Task 2-5: Flag 23 – Bust the directory part 3
$ curl -s http://172.16.222.133:1111/godzilla/
<p>Another one, you are smart ^^</p>
<p>flag23: 5vttxb43qpsh9ctbfzrd</p>
eW91IGFyZSB0b28gc21hcnQsIGRvbid0IHlvdSB0aGluay4=<br><br><br><br><br>
<font color="white">KVZWK4TOMFWWKORAM5QW2ZLPOZSXEID<style></style>sZW5nZTogODc2OSwgOTQ1MywgNjEyMywgOTkxMy4=</font>
<script language="JavaScript">
window.onload = function() {
document.addEventListener("contextmenu", function(e){
e.preventDefault();
}, false);
document.addEventListener("keydown", function(e) {
//document.onkeydown = function(e) {
// "I" key
if (e.ctrlKey && e.shiftKey && e.keyCode == 73) {
disabledEvent(e);
}
// "J" key
if (e.ctrlKey && e.shiftKey && e.keyCode == 74) {
disabledEvent(e);
}
// "S" key + macOS
if (e.keyCode == 83 && (navigator.platform.match("Mac") ? e.metaKey : e.ctrlKey)) {
disabledEvent(e);
}
// "U" key
if (e.ctrlKey && e.keyCode == 85) {
disabledEvent(e);
}
// "F12" key
if (event.keyCode == 123 || event.keyCode == 18) {
disabledEvent(e);
}
}, false);
function disabledEvent(e){
if (e.stopPropagation){
e.stopPropagation();
} else if (window.event){
window.event.cancelBubble = true;
}
e.preventDefault();
return false;
}
};
</script>
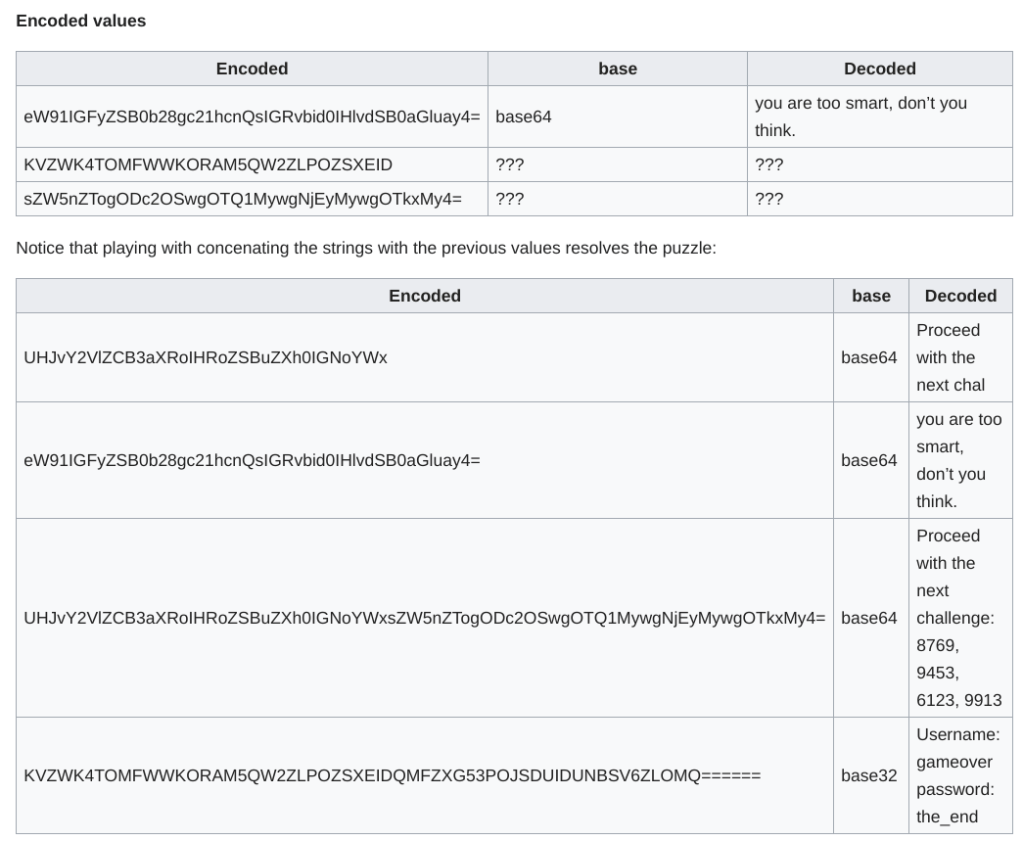
Answer: 5vttxb43qpsh9ctbfzrd
Task 2-6: Flag 24 – POP3 mail server
$ nc 172.16.222.133 9999
***************************
* Port knocking input *
***************************
Hi user, please enter the port sequence
The format is (can be more than 4): PORT PORT PORT PORT
> 8769 9453 6123 9913
Something happen
Good luck!
Yes! It unlocked port 110:
PORT STATE SERVICE
110/tcp open pop3
1111/tcp open lmsocialserver
9999/tcp open abyss
Now, let’s connect, authenticate and retrieve the emails:
$ nc 172.16.222.133 110
+OK Dovecot (Ubuntu) ready.
USER gameover
+OK
PASS the_end
+OK Logged in.
stat
+OK 4 9951
list
+OK 4 messages:
1 1010
2 7189
3 875
4 877
.
RETR 1
+OK 1010 octets
Return-Path: gameover@ctf100.com
X-Original-To: gameover@ctfmain
Delivered-To: gameover@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 601A1828E8
for ; Mon, 7 Oct 2019 12:33:52 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user gameover)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:33:52 -0000
Message-ID: <1063a6d5ad70050be0771dbfe93280a7.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:33:52 -0000
Subject: You found me
From: gameover@ctf100.com
To: gameover@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
Congratulation on finding this port, This is a pop3
Take this flag as a token of celebration.
flag 24: phzppg952hsxaarspjfs
=>From now on, thing will getting weirder and weirder. Good luck ^^
Answer: phzppg952hsxaarspjfs
Task 2-7: Flag 25 – Ook esolang
RETR 2
+OK 7189 octets
Return-Path: <gameover@ctf100.com>
X-Original-To: gameover@ctfmain
Delivered-To: gameover@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 4EB57828E8
for <gameover@ctfmain>; Mon, 7 Oct 2019 12:41:22 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user gameover)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:41:22 -0000
Message-ID: <92b46b2d9318f438d18857a060dbdef5.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:41:22 -0000
Subject: A beautiful tree
From: gameover@ctf100.com
To: gameover@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
...... .... .... .... .... .... .... .... .... .... .... .... .... .... ....
...... .... .... .... .... ...! ...? .... ...? .... .... .... ...? .... ....
...... .... .... .... .... ...? .... .... .... .... .... .... .... .... ....
...... .... .... .... .... .... ...? .... .... .... .... .... .... .... ....
...... .... .... .... .... .... .... .... .... .... .... .... ...? .... ...?
...[SNIP]...
.
So we know from the hint this is “Ook” language, with a bit of customization. Let’s make the necessary replacements:
$ sed "s/\.\.\.\.\./\.\.\./g" ook.txt | sed "s/\.\.\./Ook/g"
Now, let’s decode the message with dcode.fr:
Oak is a beautiful tree. Don't you think? flag 25: nsknvw33cx4kfzhdbveb
Answer: nsknvw33cx4kfzhdbveb
Task 2-8: Flag 26 – Rearrange the text
Hint: Look at the subject, I’m just messing it up. Time to arrange the flag. 2 6 4 3 1 5 2 6 4 3 1 5 2 6… The flag is ???..jffy3c2t. Got it?
RETR 3
+OK 875 octets
Return-Path: <gameover@ctf100.com>
X-Original-To: gameover@ctfmain
Delivered-To: gameover@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 2148B828E8
for <gameover@ctfmain>; Mon, 7 Oct 2019 12:42:35 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user gameover)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:42:35 -0000
Message-ID: <a93592815814af66d50fa39e415beee0.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:42:35 -0000
Subject: This is not over yet (264315)
From: gameover@ctf100.com
To: gameover@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
flag26: zf7b75uung8afcyfj3t2
sareunea awmkaakw
.
Open nano then copy and past the following code
nano flag26.py
#!/usr/bin/env python3
import sys
if len(sys.argv) < 3:
print("Usage: python3 {} key encoded".format(sys.argv[0]))
print("Example: python3 {} '{}' '{}'".format(
sys.argv[0], '264315', 'zf7b75uung8afcyfj3t2'))
sys.exit(1)
key = sys.argv[1]
enc = sys.argv[2].replace(' ', '')
# split encoded string into chunks of key length (last chunk may be truncated)
enc_chunk = [enc[i:i+len(key)] for i in range(0, len(enc), len(key))]
def pos_list(key, chunk):
# make pos order list (only keeps value < chunk length)
tmp = []
i = 0
for k in key:
if(int(k)<=len(chunk)):
tmp.append((int(k), i))
i+=1
tmp.sort()
pos_order = [i[1] for i in tmp]
return pos_order
dec = ""
for chunk in enc_chunk:
pos_order = pos_list(key, chunk)
for pos in pos_order:
dec += chunk[pos]
print(dec)
After copy and past the above code, press ctrl + X, then Yes to save the file
Run the file
$ python flag26.py 264315 zf7b75uung8afcyfj3t2
7zb75f8ugnaujffy3c2t
$ python flag26.py 264315 "sareunea awmkaakw"
usernamewakawaka
Answer: 7zb75f8ugnaujffy3c2t
Task 2-9: Flag 27 – Rail fence cipher
Hint: Hint on the subject. You might find the other username as well
RETR 4
+OK 877 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: gameover@ctfmain
Delivered-To: gameover@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id D7E8E828EA
for <gameover@ctfmain>; Mon, 7 Oct 2019 12:47:40 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:47:40 -0000
Message-ID: <3f6ad0edfd6b027c506da5fe1ee02a59.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:47:40 -0000
Subject: The sheep jump over two fences
From: wakawaka@ctf100.com
To: gameover@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
GONGTFA WNYEE SCKVTVVWNXSODIH LGTETSVNI VWJZNPZQWB
Use CyberChef with Rail Fence Cipher Decode (https://gchq.github.io/CyberChef/#recipe=Rail_Fence_Cipher_Decode(2,0)&input=R09OR1RGQSBXTllFRSBTQ0tWVFZWV05YU09ESUggTEdURVRTVk5JIFZXSlpOUFpRV0I) with key=2 (The sheep jump over two fences).
Decoded message: GOODNIGHT FLAG TWENTYSEVEN IS CVKWVJTZVNVPWZNQXWSB
Answer: cvkwvjtzvnvpwznqxwsb
Task 2-10: Flag 28 – Hydra bruteforce
Hint: we will, we will rock you. The text appear in between line 4500 to 5500, starts with d. It takes 1 to 2 hours to brute-force with -t 64.
We have obtained the hidden username for the POP3 mail server in the previous task. Time to brute force the password. For your information, the password of wakawaka can be found on rockyou.txt. Also, in order to minimize the brute-forcing time, the password is somehow located in between line 4500 to 5500 and we have to use the sed command to extract the line.
$ sed -n 4500,5500p /usr/share/wordlists/rockyou.txt > passwords.txt
Next, launch your hydra with the following command.
$ hydra -t 64 -l wakawaka -P wakawaka.txt pop3://<target IP>
$ sed -n 4500,5500p /data/src/wordlists/rockyou.txt | grep "^d" > passwords.txt
$ wc -l passwords.txt
38 passwords.txt
$ hydra -l wakawaka -P passwords.txt -f pop3://172.16.222.133
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-05-23 20:41:38
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 38 login tries (l:1/p:38), ~3 tries per task
[DATA] attacking pop3://172.16.222.133:110/
[110][pop3] host: 172.16.222.133 login: wakawaka password: damnit
[STATUS] attack finished for 172.16.222.133 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-05-23 20:41:47
After that, revisit the port 110 with the newly found credential.
$ nc 172.16.222.133 110
+OK Dovecot (Ubuntu) ready.
USER wakawaka
+OK
PASS damnit
+OK Logged in.
LIST
+OK 6 messages:
1 953
2 1039
3 895
4 959
5 23450
6 867
.
Read the first message and capture the flag.
RETR 1
+OK 953 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: wakawaka@ctfmain
Delivered-To: wakawaka@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 64A18828EA
for <wakawaka@ctfmain>; Mon, 7 Oct 2019 12:48:37 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:48:37 -0000
Message-ID: <28398944887e2d66a8b8b192c98a1c01.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:48:37 -0000
Subject: More stuff
From: wakawaka@ctf100.com
To: wakawaka@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
Great, you reached the abyss. If you stare into the abyss, the abyss is
staring back at you
flag 28: 3yy9e7wwe2b8fy65sgxb
The flag is clean
.
Answer: 3yy9e7wwe2b8fy65sgxb
Task 2-11: Flag 29 – SMS in the old day
This is an SMS tap code and the 3310 is referred to the famous Nokia 3310 cell phone. If you have an old phone with keypad, notice that tapping number 3 for 3 times result in letter f and 0 for space, etc. Use the online tool to decode the message.
RETR 2
+OK 1039 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: wakawaka@ctfmain
Delivered-To: wakawaka@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id F2F40828EA
for <wakawaka@ctfmain>; Mon, 7 Oct 2019 12:49:22 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:49:22 -0000
Message-ID: <37f93f2ba240bf97e89f41f47ca6bc68.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:49:22 -0000
Subject: 3310
From: wakawaka@ctf100.com
To: wakawaka@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
333 555 2 4 0 8 9 33 66 8 999 66 444 66 33 0 444 7777 0 9 7777 7 2 6 9 777
9999 44 66 222 44 777 9 777 99 33 88 5 44 0 66 33 99 8 0 7 666 777 8 0 444
7777 0 8 44 777 33 33 0 666 66 33 0 8 44 777 33 33 0 8 44 777 33 33 0 9999
33 777 666
.
Make another Python script with nano
#!/usr/bin/env python3
keys = [
[0, ' '],
[1, False],
[2, 'abc'],
[3, 'def'],
[4, 'ghi'],
[5, 'jkl'],
[6, 'mno'],
[7, 'pqrs'],
[8, 'tuv'],
[9, 'wxyz']
]
seq = "333 555 2 4 0 8 9 33 66 8 999 66 444 66 33 0 444 7777 0 9 7777 7 2 6 9 777 "
seq+= "9999 44 66 222 44 777 9 777 99 33 88 5 44 0 66 33 99 8 0 7 666 777 8 0 444 "
seq+= "7777 0 8 44 777 33 33 0 666 66 33 0 8 44 777 33 33 0 8 44 777 33 33 0 9999 "
seq+= "33 777 666"
dec = []
for s in seq.split(' '):
dec.append(keys[int(s[0])][1][len(s)-1])
print(''.join(dec))
Run the script
$ python flag29.py
flag twentynine is wspamwrzhnchrwrxeujh next port is three one three three zero
Please take note of the port number as you need it for the next stage.
Answer: wspamwrzhnchrwrxeujh
Task 2-12: Flag 30 – Keyboard shift cipher
This flag can be solved by just looking at your keyboard. For example, the left key of g is f, the left key of ; is l and etc. Or, you can just use an online decoder.
RETR 3
+OK 895 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: wakawaka@ctfmain
Delivered-To: wakawaka@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 321B0828EA
for <wakawaka@ctfmain>; Mon, 7 Oct 2019 12:49:51 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:49:51 -0000
Message-ID: <42932e91cc912e70d6fe82a44d8ff1ba.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:49:51 -0000
Subject: You are using it right now
From: wakawaka@ctf100.com
To: wakawaka@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
g;sh yjotyu od gu[dwtig[dcinueslwyk/ Mrcy [pty od gobr pmr momr doc xrtp
.
Use dcode with Keyboard Shift cipher (https://www.dcode.fr/keyboard-shift-cipher). The decoded text with a QWERTY keyboard is:
flag thirty is fypsqrufpsxubywakqtj. Next port is five one nine six zero
Answer: fypsqrufpsxubywakqtj
Task 2-13: Flag 31 – Bubble babble
This is a serial number like encoding text which is called bubble babble. Use the online decoder to decode the message.
RETR 4
+OK 959 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: wakawaka@ctfmain
Delivered-To: wakawaka@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 3F91C828EA
for <wakawaka@ctfmain>; Mon, 7 Oct 2019 12:50:26 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:50:26 -0000
Message-ID: <ee6dd2c7add823fe796bb173f66b1e56.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:50:26 -0000
Subject: Serial number
From: wakawaka@ctf100.com
To: wakawaka@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
xinik-samak-lomof-fisuf-pomyf-hytif-fosyk-kymyf-fetok-tytal-puvek-metul-byval-nasal-bynad-vymog-vunul-motyd-bosyk-zasol-gomyk-nosed-betef-casif-cisyx
There are several implementations to decode BubbleBabble (python, PHP). I found this PHP script:
$ php bubblebabble.php -d - <<< xinik-samak-lomof-fisuf-pomyf-hytif-fosyk-kymyf-fetok-tytal-puvek-metul-byval-nasal-bynad-vymog-vunul-motyd-bosyk-zasol-gomyk-nosed-betef-casif-cisyx
flag 31: 5u3rfa3vm6zzh7pzyqpe. Next port is 61111
Answer: 5u3rfa3vm6zzh7pzyqpe
Task 2-14: Flag 32 – JSFuck
This is another esolang called JSFuck. Copy the text and paste to any JSFuck translator.
RETR 5
+OK 23450 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: wakawaka@ctfmain
Delivered-To: wakawaka@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id E4AAF828EA
for <wakawaka@ctfmain>; Mon, 7 Oct 2019 12:51:13 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:51:13 -0000
Message-ID: <f3aa24146efb27ac1671aadabc9b6ef5.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:51:13 -0000
Subject: js?
From: wakawaka@ctf100.com
To: wakawaka@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])...[SNIP]...
.
I found this online decoder. Decoded message:
alert(“Flag 32 is 3j9c8utp2ag6bwbrkmkn. Next port is 10101”)
Answer: 3j9c8utp2ag6bwbrkmkn
Task 2-15: Flag 33 – ASCII shift
It is similar to the ROT cipher but involved with all ASCII code from the ASCII table. Use the following online tool to decode the message.
RETR 6
+OK 867 octets
Return-Path: <wakawaka@ctf100.com>
X-Original-To: wakawaka@ctfmain
Delivered-To: wakawaka@ctfmain
Received: from [192.168.247.144] (localhost [127.0.0.1])
by ctfmain.localdomain (Postfix) with ESMTP id 426F5828EA
for <wakawaka@ctfmain>; Mon, 7 Oct 2019 12:51:46 +0000 (UTC)
Received: from 192.168.247.129
(SquirrelMail authenticated user wakawaka)
by 192.168.247.144 with HTTP;
Mon, 7 Oct 2019 12:51:46 -0000
Message-ID: <cf4d8ccfaab21a4da45d85a4c1ce3d3b.squirrel@192.168.247.144>
Date: Mon, 7 Oct 2019 12:51:46 -0000
Subject: Definately an ASCII
From: wakawaka@ctf100.com
To: wakawaka@ctfmain
User-Agent: SquirrelMail/1.4.22
MIME-Version: 1.0
Content-Type: text/plain;charset=iso-8859-1
Content-Transfer-Encoding: 8bit
X-Priority: 3 (Normal)
Importance: Normal
Hnci"55"ku"6y6x7di9r|i|chxwx9ht0"Pgzv"rqtv"ku"54434
.
quit
+OK Logging out.
This is ASCII shift cipher (https://www.dcode.fr/ascii-shift-cipher). Decoded message:
Flag 33 is 4w4v5bg7pzgzafvuv7fr. Next port is 32212
Answer: 4w4v5bg7pzgzafvuv7fr
Task 2-16: Until the next challenge.
Did you notice the numbering on the last 5 tasks? That is the port knocking sequence for stage three. The order should be
31330 51960 61111 10101 32212
$ nc 172.16.222.133 9999
***************************
* Port knocking input *
***************************
Hi user, please enter the port sequence
The format is (can be more than 4): PORT PORT PORT PORT
> 31330 51960 61111 10101 32212
Save this sequence, you need it for stage 3
That's all for the challenge
Thank you for your participation
Answer: 31330 51960 61111 10101 32212

